We can help you in seven areas of data protection
Are you prepared for the revolution in theprotection of personal data? This really concerns you…
Does GDPR keep you awake at night? There is nothing to fear with us.
Regulatory requirements (in particular GDPR and e-IDAS) are a complex, constantly evolving area that matters to virtually every company. There is no easy solution to problems in this field. This also applies to security solutions that only cover a certain part of the related processes (IAM, SIEM, DLP, Retention management tools and the like).
That’s why we’ve decided to cover the needs of our customers with a complex set of software tools that cover broad spectrum of processes and related issues..
We address the challenge posed by GDPR through the specific process steps and tasks that are based on the Qlik Sense BI platform and our experience with data analysis gained in more than 170 successful BI projects.
GDPR intelligence for your business
EMARK Mole will help you discover your business data and to automate your sensitive data discovery
We'll help you with all processes regarding GDPR
Information Governance & Risk Management
We will help you set up the Information Governance Framework and the processes that feature decisions key to the GDPR (e.g. the right to transfer information, the right to be forgotten vs. the legally required retention policy) through our partner GlassIG and its Information Governance solution. We can also assist you with the implementation of the GDPR process into the internal control system in cooperation with our partner in the field of Risk Management Documentation and Reports or to mediate the data connection to your application.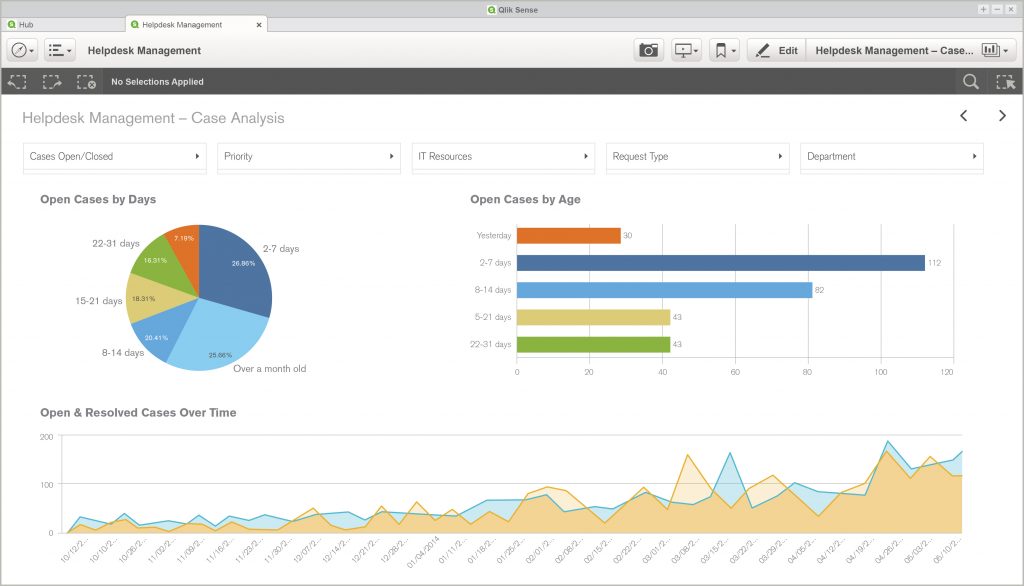
Consent & Compliance
EMARK GDPR Governance & Management Dashboard covers the most important areas that need to be managed, monitored, and evaluated from the perspective of GDPR. Through contextual and content searches our applications are able to identify where your personal and sensitive data are located, who is in charge of them and which department handles them. We use advanced technologies such as Data Lineage and Data Quality Analysis, artificial intelligence and machine learning.Security
Can you prove safe storage of your data? By law (security and privacy by default) you should. We can help you with that. We have several analytical applications and dashboards developed in cooperation with network security specialists, DLPs, or user and administrator accounts.

Privacy Impact Assessment (PIAs)
The Dashboard (mentioned in Section 1) can feature activities, verifications and PIA results that will be used in risk management activities or in managerial reporting. We can also support you by implementing the PIA itself.Big Data, research and automated decision making
Companies should document all assumptions, impacts and information and ensure that the use of personal data is consistent with the wording of Article 29 (data that are used for secondary purposes beyond the scientific, statistical and historical purpose).
Visualizations in the Dashboard may include links to the original and secondary purposes, but also the context and the relationship between the person concerned and the processor; the nature of personal data; possible consequences of processing and incorrect data processing; security measures such as functional separation, encryption, pseudonymization; as well as considerations regarding data protection implications.


Counseling and support from the responsible person
We will prepare an analytical training app that collects data from selected e-learning systems that monitor and analyse for example required GDPR skills and training; knowledge of responsible persons, employees or specialized departments; the current level of knowledge gained from a training; a continuous overview of trainings including the beginning and end of the validity of certifications; supervising the training of business and technical process owners.Violation of privacy
What if personal data is compromised? The key is not only to act quickly, the solution must also be effective. Businesses are required to keep records of any violation of the integrity of personal data stored. That is why we have prepared a set of tools ready to visualize decision trees in case of security and privacy breaches. These apps will provide detailed reports on privacy violations, including pre-made templates and forms.
